A few weeks ago, a delivery guy walked into our office. As we signed for the package, he realized that we work in cyber security and asked the following question:
“My entire music collection from the past 11 years got encrypted by ransomware. Is there anything I can do about it?
They’re asking for $500 for the decryption key.”
“Do you have a backup?”
He looked down and said a bitter “no.”
This scenario is unfolding right now somewhere in the world. Maybe even in your city or neighborhood. In this very moment, someone is clicking a link in a spam email or activating macros in a malicious document. In a few seconds, all their data will be encrypted and they’ll have just a few days to pay hundreds of dollars to get it back. Unless they have a backup, which most people do not have.
Ransomware creators and other cyber criminals involved in the malware economy are remorseless. They’ve automated their attacks to the point of targeting anyone and everyone.
Take this story from the New York Times:
“My mother received the ransom note on the Tuesday before Thanksgiving. It popped up on her computer screen soon after she’d discovered that all of her files had been locked. “Your files are encrypted,” it announced. “To get the key to decrypt files you have to pay 500 USD.”
If my mother failed to pay within a week, the price would increase to $1,000. After that, her decryption key would be destroyed and any chance of accessing the 5,726 files on her PC – essentially all of her data – would be lost forever.
Sincerely,
CryptoWall
Prevention is absolutely the best security strategy in this case, and to help you understand what you’re up against, we’ve packed this guide with a host of information.
- What ransomware is
- How it evolved
- Who ransomware creators target the most
- How ransomware spreads through the web
- How ransomware infections occur
- Why it often goes undetected by antivirus
- The most notorious ransomware families
- How to set up the best protection
- How to decrypt your data without paying ransom
So What is Ransomware?
You shouldn’t feel helpless when thinking of the crushing effects of ransomware. There are many practical provisions you can take to block or limit the impact of cyber attacks on your data. And we’re about to show you just what to do.
Ransomware is a sophisticated piece of malware that blocks the victim’s access to his/her files.
There are two types of ransomware in circulation:
Encrypting ransomware, which incorporates advanced encryption algorithms. It’s designed to block system files and demand payment to provide the victim with the key that can decrypt the blocked content. Examples include CryptoLocker, Locky, CrytpoWall and more.
Locker ransomware, which locks the victim out of the operating system, making it impossible to access the desktop and any apps or files. The files are not encrypted in this case, but the attackers still ask for a ransom to unlock the infected computer. Examples include the police-themed ransomware or Winlocker.
Another version pertaining to this type is the Master Boot Record (MBR) ransomware. The MBR is the section of a PC’s hard drive which enables the operating system to boot up. When MBR ransomware strikes, the boot process can’t complete as usual, and prompts a ransom note to be displayed on the screen. Examples include Satana and Petya ransomware.
However, the most widespread type of ransomware is crypto-ransomware or encrypting ransomware, which we will focus on in this guide. The cyber security community agrees that this is the most prominent and worrisome cyber threat of the moment.
Ransomware has some key characteristics that set it apart from other malware:
- It features unbreakable encryption, which means that you can’t decrypt the files on your own (there are various decryption tools released by cyber security researchers – more on that later);
- It has the ability to encrypt all kinds of files, from documents to pictures, videos, audio files and other things you may have on your PC;
- It can scramble your file names, so you can’t know which data was affected. This is one of the social engineering tricks used to confuse and coerce victims into paying the ransom;
- It will add a different extension to your files, to sometimes signal a specific type of ransomware strain;
- It will display an image or a message that lets you know your data has been encrypted and that you have to pay a specific sum of money to get it back;
- It requests payment in Bitcoins, because this crypto-currency cannot be tracked by cyber security researchers or law enforcements agencies;
- Usually, the ransom payments has a time-limit, to add another level of psychological constraint to this extortion scheme. Going over the deadline typically means that the ransom will increase, but it can also mean that the data will be destroyed and lost forever.
- It uses a complex set of evasion techniques to go undetected by traditional antivirus (more on this in the “Why ransomware often goes undetected by antivirus” section);
- It often recruits the infected PCs into botnets, so cyber criminals can expand their infrastructure and fuel future attacks;
- It can spread to other PCs connected in a local network, creating further damage;
- It frequently features data exfiltration capabilities, which means that ransomware can extract data from the affected computer (usernames, passwords, email addresses, etc.) and send it to a server controlled by cyber criminals;
- It sometimes includes geographical targeting, meaning the ransom note is translated into the victim’s language, to increase the chances for the ransom to be paid.
The inventory of things that ransomware can do keeps growing every day, with each new security alert broadcasted by our team or other malware researchers. As ransomware families and variants multiply, you need to understand that you need at least baseline protection to avoid data loss and other troubles.
The History of Ransomware
Encrypting ransomware is a complex and advanced cyber threat which uses all the tricks available because it makes cyber criminals a huge amount of money. We’re talking millions!
If you’re curious how it all started, it’s time to go over a quick history of ransomware. It may be difficult to imagine, but the first ransomware in history emerged in 1989 (that’s 27 years ago). It was called the AIDS Trojan, whose modus operandi seems crude nowadays. It spread via floppy disks and involved sending $189 to a post office box in Panama to pay the ransom.
How times have changed!
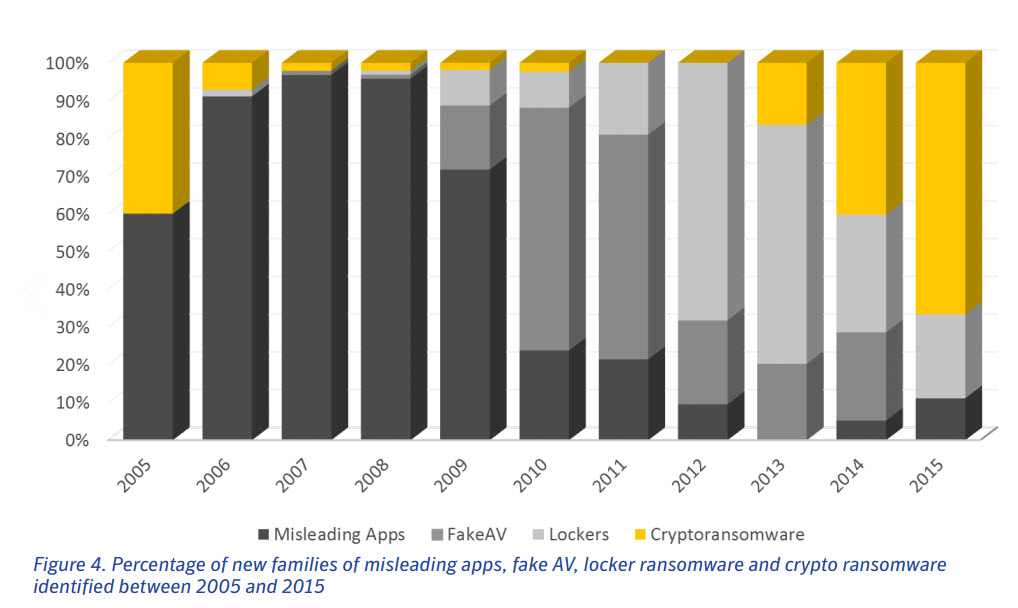
As cyber criminals moved from cyber vandalism to cyber crime as a business, ransomware emerged as the go-to malware to feed the money-making machine. The advent of Bitcoin and evolution of encryption algorithms favored made the context ripe for ransomware development too. This graph shows just how many types of encrypting malware researchers have discovered in the past 10 years.
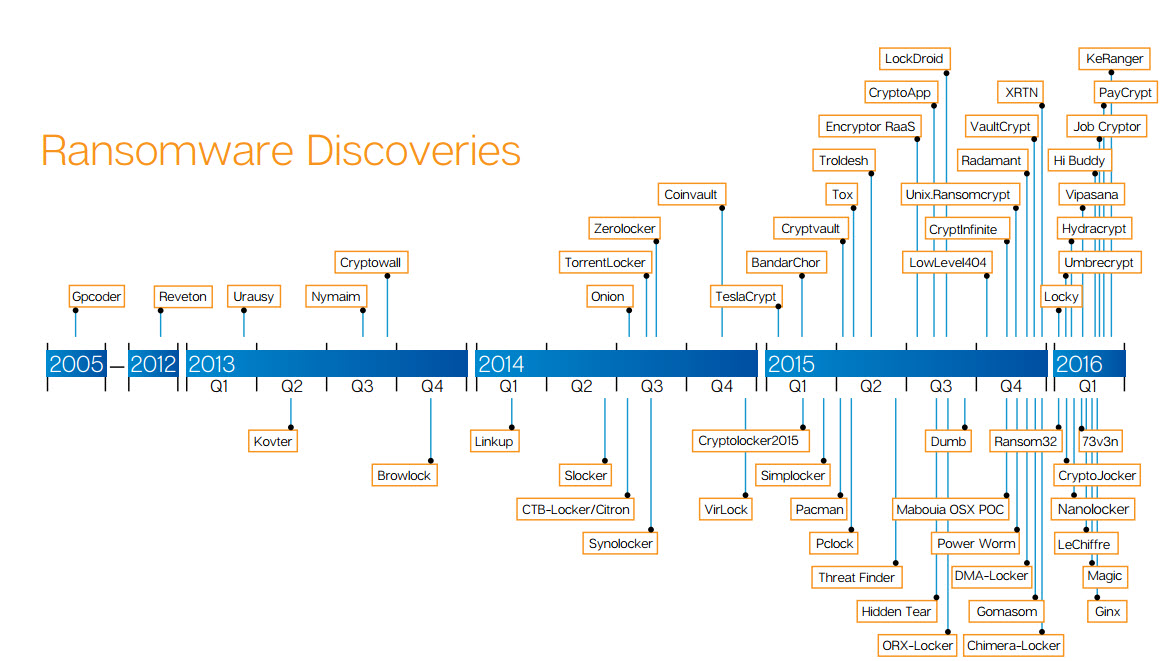
And keep in mind 3 things, so you can get a sense of how big the issue really is:
- Many variants exist for each type (for example, CrytpoWall is on its 4th version);
- No one can map all the existing ransomware out there (because most ransomware attacks go unreported);
- New ransomware is coming out in volumes at an ever-increasing pace.
As you can see, things escalated quickly and the trend continues to grow.
Top Targets for Ransomware Creators & Distributors
Cyber criminals are not just malicious hackers who want public recognition, nor are they driven by their quest for cyber mischief. They are business-oriented and seek to profit from their efforts. After testing ransomware our on home users and evaluating the impact, they moved on to bigger targets including police departments, city councils, schools and hospitals. Clearly ethics or morality have no weight in today’s money-hungry cyber crime business. “There is honor among thieves” was tossed out the window a long time ago.
That leaves us with to dig out the reasons why online criminals choose to target various types of Internet users. This may help you better understand why things happen as they do right now.
Why they target home users:
- Because they don’t have data backups;
- Because they have little or no cyber security education, which means they’ll click on almost anything;
- Because the same lack of online safety awareness makes them prone to manipulation by cyber attackers;
- Because they lack even baseline cyber protection;
- Because they don’t keep their software up to date (even if specialists always nag them to);
- Because they fail to invest in need-to-have cyber security solutions;
- Because they often rely on luck to keep them safe onlineBecause most home users still rely exclusively on antivirus to protect them from all threats, which is frequently ineffective in spotting and stopping ransomware;
- Because of the sheer volume of Internet users that can become potential victims (more infected PCs = more money).
Why they target businesses:
- Because that’s where the money is;
- Because attackers know that ransomware can cause major business disruptions, which will increase their chances of getting paid;
- Because computer systems in companies are often complex and prone to vulnerabilities that can be exploited through technical means;
- Because the human factor is still a huge liability which can also be exploited, but through social engineering tactics;
- Because ransomware can affect not only computers, but also servers and cloud-based file-sharing systems, going deep into a business’s core;
- Because cyber criminals know that business would rather not report ransomware attacks for fears of legal or reputation-related consequences;
- Because small businesses are often unprepared to deal with advanced cyber attacks (which ransomware is) and have a lax BYOD (bring your own device) policy.
Why they target public institutions:
- Because public institutions, such as government agencies, manage huge databases of personal and confidential information that cyber criminals can sell;
- Because these institutions oft times lack appropriate cyber defenses that can protect them against ransomware;
- Because the staff is not trained to spot and avoid cyber attacks (ransomware often leverages the human factor weakness to trigger the infection);
- Because public institutions often use outdated software and equipment, which means that their computer systems are packed with security holes just begging to be exploited;
- Because ransomware has a big impact on conducting usual activities, causing huge disruptions;
- Because successfully attacking public institutions feeds the cyber criminals’ egos (they may want money above all else, but they won’t hesitate to reinforce their position in the community about attacking a high-profile target).
No Platform is Immune
In terms of platforms and devices, ransomware doesn’t discriminate either. We have ransomware tailor-made for personal computers (too many types to count, but more on that in “The most notorious ransomware families” section), mobile devices (with Android as the main victim and a staggering growth) and servers. And when it comes to servers, the attack is downright vicious.
“Some groups do this by infiltrating the target server and patching the software so that the stored data is in an encrypted format where only the cyber criminals have the key to decrypt the data. The premise of this attack is to silently encrypt all data held on a critical server, along with all of the backups of the data. This process may take some time, depending on the organization, so it requires patience for the cyber criminals to carry it out successfully. Once a suitable number of backups are encrypted, the cybercriminals remove the decryption key and then make their ransom demands known, which could be in the order of tens of thousands of dollars.”
Source: The evolution of ransomware by Symantec
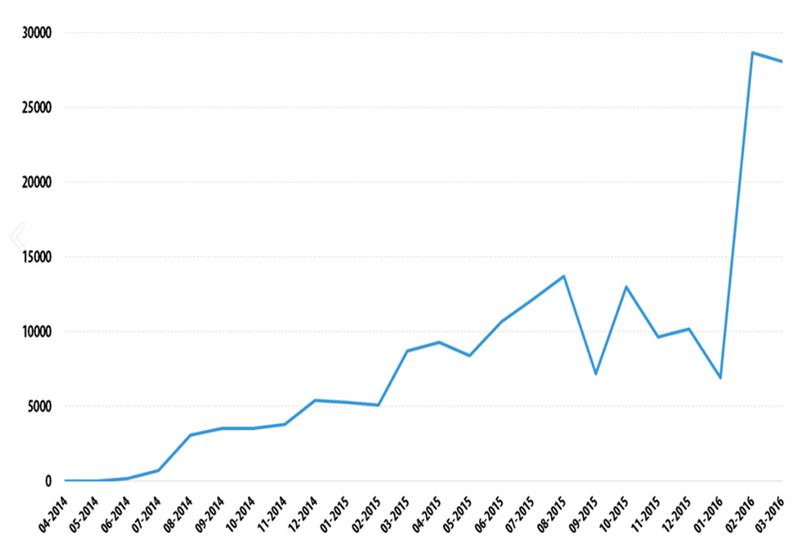
This prompted the FBI and many other institutions and security vendors in the industry to urge users, companies and other decision-makers to prepare against this threat and set up strong cyber protection layers.
Attacks on critical infrastructure (electricity, water, etc.) could be next, and even the thought of that can make anyone shudder.
How do ransomware threats spread?
Ransomware and any other advanced piece of financial or data stealing malware spreads by any available means. Cyber criminals simply look for the easiest way to infect a system or network and use that backdoor to spread the malicious content.
Nevertheless, these are the most common methods used by cybercriminals to spread ransomware:
- Spam email campaigns that contain malicious links or attachments (there are plenty of forms that malware can use for disguise on the web);
- Security exploits in vulnerable software;
- Internet traffic redirects to malicious websites;
- Legitimate websites that have malicious code injected in their web pages;
- Drive-by downloads;
- Malvertising campaigns;
- SMS messages (which apply to ransomware that targets mobile devices);
- Botnets;
- Self-propagation (spreading from one infected computer to another);
- Affiliate schemes in ransomware-as-a-service (earning a share of the profits by helping further spread ransomware).
Crypto-ransomware attacks employ a subtle mix of technology and psychological manipulation (also known as social engineering).
These attacks get more refined by the day, as cyber criminals learn from their mistakes and tweak their malicious code to be stronger, more intrusive and better suited to avoid cyber security solutions.That’s why each new ransomware variant is a bit different from its forerunner. Malware creators incorporate new evasion tactics and pack their “product” with piercing exploit kits, pre-coded software vulnerabilities to target and more.
For example, here is how online criminals find vulnerable websites, inject malicious JavaScript code in them and use this trigger to redirect potential victims to infected websites.
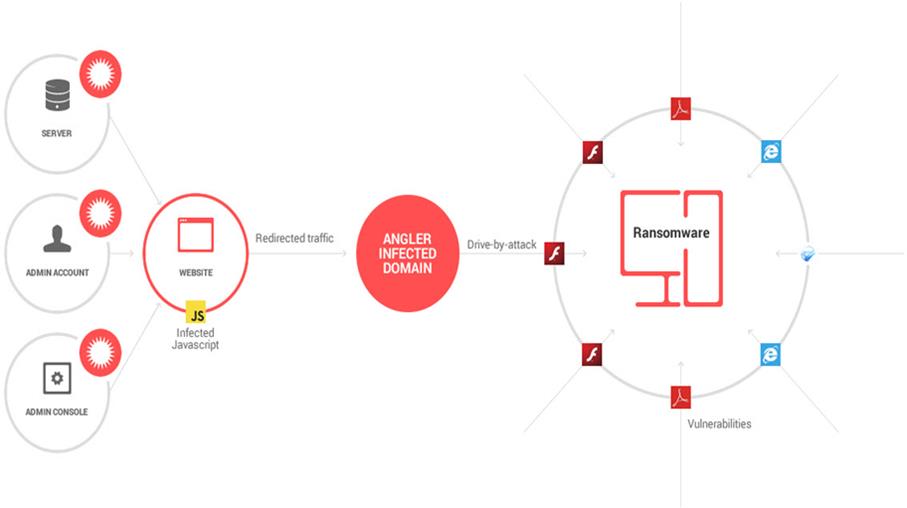
And here is how infections happen…
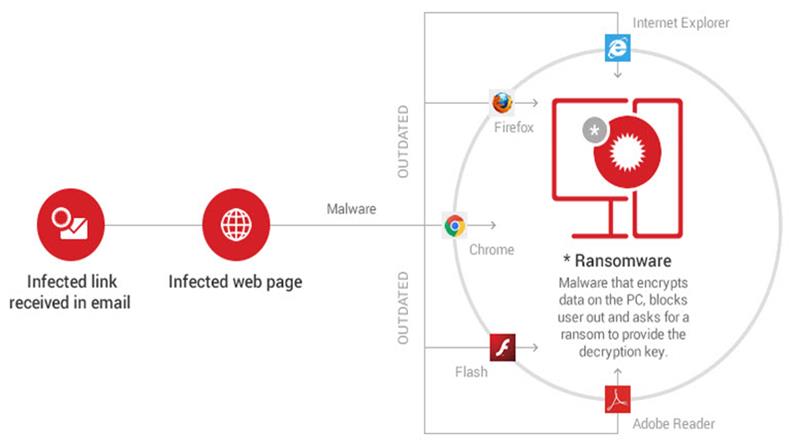
How Infections Happen
Initially, the victim receives an email which includes a malicious link or a malware-laden attachment. Alternatively, the infection can originate from a malicious website that delivers a security exploit to create a backdoor on the victim’s PC by using a vulnerable software from the system. If the victim clicks on the link or downloads and opens the attachment, a downloader (payload) will be placed on the affected PC. The downloader uses a list of domains or C&C servers controlled by cyber criminals to download the ransomware program on the system. The contacted C&C server responds by sending back the requested data, in our case, the ransomware. The ransomware starts to encrypt the entire hard disk content, personal files and sensitive information. Everything, including data stored in cloud accounts (Google Drive, Dropbox) synced on the PC. It can also encrypt data on other computers connected in the local network. A warning pops up on the screen with instructions on how to pay for the decryption key.
Everything happens in just a few seconds, so victims are completely dumbstruck as they stare at a ransom note in disbelief. Most of them feel betrayed, because they can’t seem to understand one thing:
“But I have antivirus! Why didn’t it protect me from this?”
Be that as it may, ransomware often goes undetected by antivirus and the longer a malware infection can persist on a compromised PC, the more data it can extract and the more damage it can do.
So here are just a few of the tactics that ransomware employs to remain covert and maintain the anonymity of its makers and distributors:
- Communication with Command & Control servers is encrypted and difficult to detect in network traffic;
- It features built-in traffic anonymizers, like TOR and Bitcoin, to avoid tracking by law enforcement agencies and to receive ransom payments;
- It uses anti-sandboxing mechanisms so that antivirus won’t pick it up;
- It employs domain shadowing to conceal exploits and hide the communication between the downloader (payload) and the servers controlled by cyber criminals (where the ransomware is stored);
- It features Fast Flux, another technique used to keep the source of the infection anonymous;
- It deploys encrypted payloads which can make it more difficult for antivirus to see that they include malware, so the infection has more time to unfold;
- It has polymorphic behavior that endows the ransomware with the ability to mutate enough to create a new variant, but not so much as to alter the malware’s function;
- It has the ability to remain dormant – the ransomware can remain inactive on the system until the computer it at its most vulnerable moment and take advantage of that to strike fast and effectively.
The Most Notorious Ransomware Families:
By now you know that there’s plenty of ransomware out there. With names such as CryptXXX, Troldesh or Chimera, these strains sound like the stuff hacker movies are made of. So while newcomers may want to get a share of the cash, there are some ransomware families that have established their domination. If you find any similarities between this context and how the mafia conducts its business, well, it’s because they resemble in some aspects.
Reveton
In 2012, the major ransomware strand known as Reveton started to spread. It was based on the Citadel trojan, which was, in turn, part of the Zeus family. This type of ransomware has become known to display a warning from law enforcement agencies, which made people name it “police trojan” or “police virus“. This was a type of locker ransomware, not an encrypting one. Once the warning appears, the victim is informed that the computer has been used for illegal activities, such as torrent downloads or for watching porn .The graphic display enforced the idea that everything is real. Elements like the computer IP address, logo from the law enforcement organization in that specific country or the localized content, all of these created the general illusion that everything is actually happening.
Brian Krebs published larger analysis on Reveton, indicated that security exploits have been used by cybercriminals and that:
“insecure and outdated installations of Java remain by far the most popular vehicle for exploiting PCs.”
CryptoLocker
In June 2014, Deputy Attorney General James Cole, from the US Department of Justice, declared that a large joint operation between law agencies and security companies employed:
“traditional law enforcement techniques and cutting edge technical measures necessary to combat highly sophisticated cyber schemes targeting our citizens and businesses.”
He was talking about Operation Tovar, one of the biggest take-downs in the history of cyber security, which Heimdal Security also participated in. Operation Tovar aimed to take down the Gameover ZeuS botnet, which authorities also suspected of spreading financial malware and CryptoLocker ransomware. As Brian Krebs mentioned in his take on this ransomware family:
“The trouble with CryptoLocker is not so much in removing the malware — that process appears to be surprisingly trivial in most cases. The real bummer is that all of your important files — pictures, documents, movies, MP3s — will remain scrambled with virtually unbreakable encryption…”
CryptoLocker infections peaked in October 2013, when it was infecting around 150,000 computers a month! Since then, there have been sightings of CryptoLocker in numerous campaigns spoofing postal or delivery services in northern Europe.
CryptoWall
Though the CryptoLocker infrastructure may have been temporarily down, it doesn’t mean that cybercriminals didn’t find other methods and tools to spread similar ransomware variants. CryptoWall is such a variant and it has already reached its third version, CryptoWall 4.0. This number alone shows how fast this malware is being improved and used in online attacks!
In 2015, even the FBI agreed that ransomware is here to stay. This time, it wouldn’t stop to home computers, but it will spread to infect:
“Businesses, financial institutions, government agencies, academic institutions, and other organizations… resulting in the loss of sensitive or proprietary information.”
Until then, this prediction became reality and now we understand the severity and impact of the crypto-ransomware phenomenon. In the similar manner to CryptoLocker, CryptoWall spreads through various infection vectors since, including browser exploit kits, drive-by downloads and malicious email attachments.
CTB-Locker
CTB Locker is one of the latest ransomware variants of CryptoLocker, but at a totally different level of sophistication.
Let’s take a quick look at its name: what do you think CTB stands for?
C comes from Curve, which refers to its persistent Elliptic Curve Cryptography that encodes the affected files with a unique RSA key;
T comes from TOR, because it uses the famous P2P network to hide the cybercriminals’ activity from law enforcement agencies;
B comes from Bitcoin, the payment method used by victims to pay the ransom, also designed to hide the attackers’ location.
What’s also specific to CTB-locker is that is includes multi-lingual capabilities, so attackers can use it to adapt their messaging to specific geographical areas. If more people can understand what happened to their data, the bigger the payday.
CTB-Locker was one of the first ransomware strains to be sold as a service in the underground forums. Since then, this has become almost the norm, but two years ago it was an emerging trend. Now, potential cyber criminals don’t really need strong technical skills, as they can purchase ready-made malware which include even dashboard where they can track their successful infections and return on investment.
In 2014, malware analyst Kafeine managed to access one of these black markets and posted all the information advertised by online criminals. By taking a quick look at the malware creators’ ad, we can see that the following support services are included into the package:
- instructions on how to install the Bitcoin payment on the server;
- how to adjust the ransomware settings in order to target the selected victims;
- details such as the requested price and the localized language that should be used; recommendations on the price that you can set for the decryption key. Heimdal Security specialists noticed that CTB Locker spreads through spam campaigns, where the e-mail message appears as an urgent FAX message.
This is a sample of the e-mail content:
From: Spoofed / falsified content Subject:Fax from RAMP Industries Ltd Incoming fax, NB-112420319-8448New incoming fax message from +07829 062999[Fax server]= +07955-168045[Fax server]: [Random ID] Content: No.: +07434 20 65 74Date: 2015/01/18 14:56:54 CST
TorrentLocker
This file-encrypting ransomware emerged in early 2014 and its makers often tried to refer to it as CryptoLocker, in order to piggyback on its awareness. Since then, TorrentLocker relied almost entirely on spam emails for distribution. In order to increase effectiveness, both the emails and the ransom note were targeted geographically. Attackers noticed that attention to detail meant that they could trick more users into opening emails and clicking on malicious links, to they took it a step further. They used good grammar in their texts, which made their traps seem authentic to the unsuspecting victims.
TorrentLocker creators proved that they were attentively looking at what’s going on with their targeted “audience” when they corrected a flaw in their encryption mechanism. Until that point, a decryption tool created by a malware researcher had worked. But soon they released a new variant which featured stronger encryption and narrowed the chances for breaking it to zero. Its abilities to harvest email addresses from the infected PC are also noteworthy. Naturally, these emails were used in subsequent spam campaigns to further distribute the ransomware.
Locky
First spotted in February 2016, this ransomware strain made its entrance with a bang by extorting a hospital in Hollywood for about $17,000. Since then, Locky has a rampant distribution across the world. Its descendant, Zepto, made its debut the same year.
What’s Next?
We cannot guess what future ransomware names will be, but we can expect to see one trend among cyber criminals: more target attacks with more advance preparation and those that need smaller infrastructure for deployment. So let’s take a look at what you can do to safeguard yourself against these attacks.
Locally on a PC:
- Don’t store important data only on your PC
- Have 2 backups of your data: on an external hard drive and in the cloud – Dropbox/Google Drive/etc.
- Leave your Dropbox/Google Drive/OneDrive/etc. application off and only open them once a day, to sync data, and close them once this is done.
- Keep your operating system and the software up to date, including the latest security updates.
- For daily use, don’t use an administrator account on your computer. Use a guest account with limited privileges.
- Turn off macros in the Microsoft Office suite – Word, Excel, PowerPoint, etc. In the browser
- Remove the following plugins from your browsers: Adobe Flash, Adobe Reader, Java and Silverlight. If you absolutely must use them, set the browser to ask you if you want to activate these plugins when needed.
- Adjust your browsers’ security and privacy settings for increased protection
- Remove outdated plugins and add-ons from your browsers. Keep only the ones you use on a daily basis and keep them updated to the latest version.
- Use an ad blocker to avoid the threat of potentially malicious ads.
Online:
- Never open spam emails or emails from unknown senders
- Never download attachments from spam emails or suspicious emails
- Never click links in spam emails or suspicious emails.
Anti-ransomware security tools:
- Use a reliable, paid antivirus product that includes an automatic update module and a real-time scanner
- Understand the importance of having a traffic-filtering solution that can provide proactive anti-ransomware protection.
Should You Ever Pay the Ransom? NO!
Paying the ransom gives you no guarantee that the online criminals at the other end of the Bitcoin transfer will give you the decryption key. And even if they do, you’d be further funding their greedy attacks and fueling the never-ending malicious cycle of cyber crime.
How to get your data back without paying the ransom:
There hundreds of types of ransomware out there, but cyber security researchers are working around the clock to break the encryption that at least some of them use. Unfortunately, the most notorious families have proven to be unbreakable so far. In spite of this, there are many other cryptoware strains that are not that well coded and which specialists were able to crack. It is a never-ending battle though, which is why we urge you to focus on prevention and having multiple backups for your data.
Conclusion:
Ransomware brought extortion to a global scale, and it’s up to all of us, users, business-owners and decision-makers, to disrupt it.
We now know that:
- creating malware or ransomware threats is now a business and it should be treated as such;
- the “lonely hacker in the basement” stereotype died long time ago;
- the present threat landscape is dominated by well defined and well funded groups that employ advanced technical tools and social engineering skills to access computer systems and networks;
- even more, cyber criminal groups are hired by large states to target not only financial objectives, but political and strategic interests.
We also know that we’re not powerless and there’s a handful of simple things we can do to avoid ransomware. Cyber criminals have as much impact over your data and your security as you give them.
Stay safe and don’t forget the best protection is always a backup!
Questions?
Contact Scott Oleson, Senior VCIO/IT Director
soleson@fbponline.wpengine.com Tel: 303.390.3600



